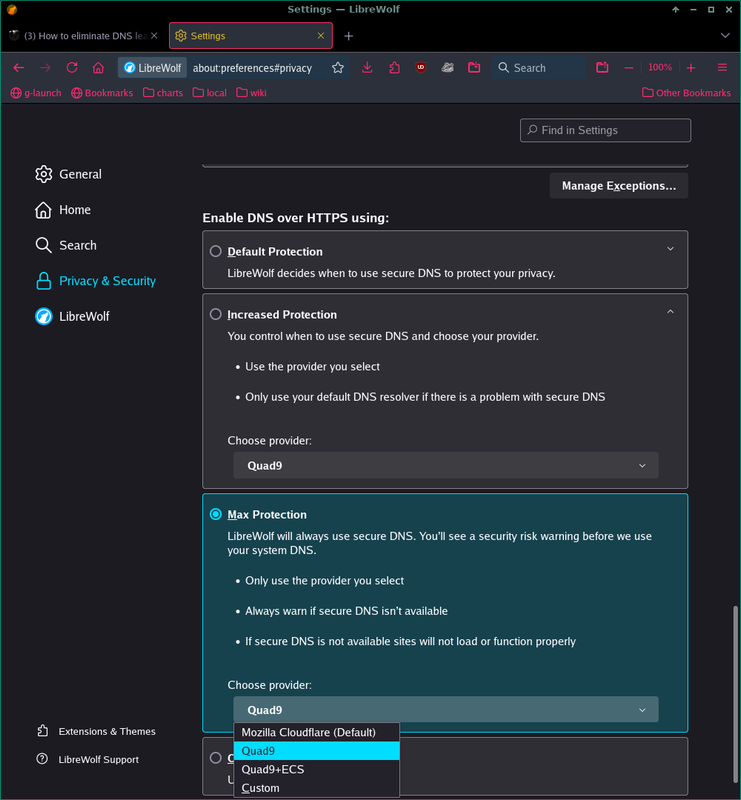
How to eliminate DNS leaks? [Bookworm64_10.0.6]
I discovered I have DNS leaks, and apparently all of them are going to google. Looks like my internet provider is using google servers for DNS.
I tried to find out more and what I can do about it. Can anyone shed any light on this?
First stop:
https://dnscrypt.info/implementations/
Second stop:
https://github.com/DNSCrypt/dnscrypt-proxy
Third stop:
https://github.com/dnscrypt/dnscrypt-pr ... tion-linux
Fourth stop:
https://github.com/dnscrypt/dnscrypt-pr ... and-Ubuntu
Fifth stop:
https://github.com/dnscrypt/dnscrypt-pr ... tion-linux
I did not get further than Step 2 on this page.
Below are my results.
Code: Select all
# ss -lp 'sport = :domain'
Command 'ss' not found, but can be installed with:
apt install iproute2
# apt install iproute2
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following package was automatically installed and is no longer required:
libxaw3dxft6
Use 'apt autoremove' to remove it.
The following additional packages will be installed:
libbpf1 libcap2-bin
Suggested packages:
iproute2-doc
Recommended packages:
libatm1 libpam-cap
The following NEW packages will be installed:
iproute2 libbpf1 libcap2-bin
0 upgraded, 3 newly installed, 0 to remove and 39 not upgraded.
Need to get 1,226 kB of archives.
After this operation, 4,129 kB of additional disk space will be used.
N: Ignoring file 'mullvad.listlear' in directory '/etc/apt/sources.list.d/' as it has an invalid filename extension
N: Ignoring file 'mullvad.listclear' in directory '/etc/apt/sources.list.d/' as it has an invalid filename extension
Do you want to continue? [Y/n] y
Get:1 http://deb.debian.org/debian bookworm/main amd64 libbpf1 amd64 1:1.1.0-1 [145 kB]
Get:2 http://deb.debian.org/debian bookworm/main amd64 libcap2-bin amd64 1:2.66-4 [34.7 kB]
Get:3 http://deb.debian.org/debian bookworm/main amd64 iproute2 amd64 6.1.0-3 [1,046 kB]
Fetched 1,226 kB in 0s (4,648 kB/s)
debconf: delaying package configuration, since apt-utils is not installed
Selecting previously unselected package libbpf1:amd64.
(Reading database ... 61375 files and directories currently installed.)
Preparing to unpack .../libbpf1_1%3a1.1.0-1_amd64.deb ...
Unpacking libbpf1:amd64 (1:1.1.0-1) ...
Selecting previously unselected package libcap2-bin.
Preparing to unpack .../libcap2-bin_1%3a2.66-4_amd64.deb ...
Unpacking libcap2-bin (1:2.66-4) ...
Selecting previously unselected package iproute2.
Preparing to unpack .../iproute2_6.1.0-3_amd64.deb ...
Unpacking iproute2 (6.1.0-3) ...
dpkg: error processing archive /var/cache/apt/archives/iproute2_6.1.0-3_amd64.deb (--unpack):
cannot copy extracted data for './sbin/devlink' to '/sbin/devlink.dpkg-new': failed to write (No space left on device)
dpkg: error: error creating new backup file '/var/lib/dpkg/status-old': No space left on device
E: Sub-process /usr/bin/dpkg returned an error code (2)
# apt autoremove ibxaw3dxft6
N: Ignoring file 'mullvad.listlear' in directory '/etc/apt/sources.list.d/' as it has an invalid filename extension
N: Ignoring file 'mullvad.listclear' in directory '/etc/apt/sources.list.d/' as it has an invalid filename extension
E: dpkg was interrupted, you must manually run 'dpkg --configure -a' to correct the problem.
# run dpkg --configure -a
Command 'run' not found, did you mean:
command 'zun' from deb python3-zunclient
command 'rup' from deb rstat-client
command 'runc' from deb runc
command 'runq' from deb exim4-daemon-heavy
command 'runq' from deb exim4-daemon-light
command 'srun' from deb slurm-client
command 'crun' from deb crun
command 'grun' from deb grun
command 'zrun' from deb moreutils
Try: apt install <deb name>
I did download the file:
https://github.com/DNSCrypt/dnscrypt-pr ... 1.5.tar.gz