Page 4 of 5
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 4:51 pm
by fredx181
tammi806 wrote: ↑Tue Sep 05, 2023 4:34 pm
I think I'm just going to stay with using Easy OS.
I install it and it works OOTB.
To update Easy OS I click on the update icon on the desktop.
I just ain't got the patience for all of this anymore.
I'm an install and use type of user.
I really appreciate the help and replies but just more than I want to deal with at my age.
Thanks again. 
There are many responses on your question, apparently "run-as-root" (or not) is a big issue in general (and lots of different opinions), you may want to ignore some replies as they may not have anything to do with your way of using Puppy, anyway, stay safe (and healthy) and good luck!
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 5:40 pm
by wizard
@tammi806
What you are suggesting isn't that similar to running as live version in ram as PUPMODE=5 with the changes to harden the browser.
If "running as live version" is referencing USB booting, then yes. Live version could also be from CD/DVD. Running without a savefile is PUPMODE=5 regardless of the boot media. In the outline above two things that improve usability and enhance the security are:
1. Locking down any customization with nicOS-Utility_Suite
2. Removing the media after use
There are additional techniques that can be used, some do require more time and skill to implement and some add constraints.
One that is suggested is installing Puppy to read only or write protected media such as CD, DVD, or USB/SD card with write protection. My personal choice is a SD card w/write protect switch, that is then used in a SD card to USB adapter. That combo is effective, economical and can be easily changed or upgraded.
Thanks
wizard
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 6:23 pm
by tammi806
wizard wrote: ↑Tue Sep 05, 2023 5:40 pm
@tammi806
What you are suggesting isn't that similar to running as live version in ram as PUPMODE=5 with the changes to harden the browser.
If "running as live version" is referencing USB booting, then yes. Live version could also be from CD/DVD. Running without a savefile is PUPMODE=5 regardless of the boot media. In the outline above two things that improve usability and enhance the security are:
1. Locking down any customization with nicOS-Utility_Suite
2. Removing the media after use
There are additional techniques that can be used, some do require more time and skill to implement and some add constraints.
One that is suggested is installing Puppy to read only or write protected media such as CD, DVD, or USB/SD card with write protection. My personal choice is a SD card w/write protect switch, that is then used in a SD card to USB adapter. That combo is effective, economical and can be easily changed or upgraded.
Thanks
wizard
I don't mind running as a live version from ram and then removing the media loaded from as I always thought that was one of the really cool things about using Puppy Linux.
I don't save when I do online things.
The few places I do any personal business with will have copies of any transactions.
I'm aware that ain't bullet proof and can also be had if whoever wants it and is determined to get it.
I to have SD cards that fit into a card reader/writer I have that plugs into a USB jack.
Where do I learn about using this nicOS-Utility_Suite.
I'm not one to just give up.
Trying to understand everything posted and became confused, frustrated and PO so my apologies to everyone for that.
Thanks 
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 6:50 pm
by Chelsea80
@ tammi806
From here you can download nicOS-Utility-Suite -
viewtopic.php?p=12983#p12983
This is the latest version I can find, but then I might be wrong -
Best regards
Chelsea80
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 6:54 pm
by rockedge
Trying to understand everything posted and became confused, frustrated and PO so my apologies to everyone for that.
I think many of us totally understand. Not a problem to ask for any clarifications. We'll stick to it until your successful.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 6:55 pm
by Burunduk
Sorry for the off-topic post here.
dimkr wrote: ↑Tue Sep 05, 2023 3:25 pm
ls -la secret.txt
-rw-r--r-- 1 root root 36 Sep 5 15:27 secret.txt
...
I can recommend only Puppy where this simple test results in "permission denied"
May I ask why it should result in permission denied? The file (as well as the directory) is world readable, isn't it?
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 6:57 pm
by williwaw
tammi806 wrote: ↑Tue Sep 05, 2023 4:34 pm
I think I'm just going to stay with using Easy OS.
I install it and it works OOTB.
To update Easy OS I click on the update icon on the desktop.
I just ain't got the patience for all of this anymore.
I'm an install and use type of user.
I really appreciate the help and replies but just more than I want to deal with at my age.
Thanks again. :)
With EasyOs, your Firefox should already run as a different user. Look in /mnt/home and you should see different apps each running as their own user. This is a different security model from puppy. Easy also has the capability of running apps in containers, and also has other security schemas
https://www.google.com/search?q=secure& ... org%2Fnews
Easy still has the user spot and the script run-as-spot. The run-as-spot script in Easy fails to bring up a dialog but does change the user to spot in the terminal. I do not know what purpose it serves in Easy,
Perhaps Puppy should adopt some of Barrys improvements.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:04 pm
by dimkr
Burunduk wrote: ↑Tue Sep 05, 2023 6:55 pm
May I ask why it should result in permission denied? The file (as well as the directory) is world readable, isn't it?
spot should not be able to read files under /root!
Imagine you're running a password manager (or some other applications which stores private or sensitive information) as root, but running your browser as spot.
If spot can read those files from /root, a browser vulnerability may provide an attacker with access to sensitive information, so the security benefit of running your browser as spot is smaller. (For example, spot still can't implant a malicious MBR or change UEFI settings.)
If spot can write files under /root, spot hardly provides any security benefit over running as root, because an attacker can modify /root/.profile, /root/.xinitrc (and many other files) to run commands as root.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:11 pm
by williwaw
dimkr wrote: ↑Tue Sep 05, 2023 3:25 pm
Booted a clean VM with the top option offered in puppylinux.com, "FossaPup64 9.5", and this is what I see:
Are there newer versions of run-as-spot than the one found in FossaPup64 9.5?
If so, then where would you expect to find it?
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:12 pm
by Burunduk
dimkr wrote: ↑Tue Sep 05, 2023 7:04 pm
spot should not be able to read files under /root!
Thanks for the response. I've found the difference already. /root is 700 in voidpup but 755 in fossapup64-9.5.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:19 pm
by fredx181
dmkir wrote:If spot can write files under /root, ....
How ? You mean if secret.txt contains the root password ?
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:22 pm
by dimkr
fredx181 wrote: ↑Tue Sep 05, 2023 7:19 pm
dmkir wrote:If spot can write files under /root, ....
How ? You mean if secret.txt contains the root password ?
No, every time X starts, xinit runs /root/.xinitrc, and every time root runs a shell, it runs /root/.bashrc, and every time the window manager is started, it runs the scripts in /root/Startup. If spot can write to any of these, an attacker that is able to execute arbitrary code inside an applications running as spot can write a script that will eventually run as root.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:30 pm
by wizard
@tammi806
If you have a USB stick with a write protect switch (generally expensive) or a SD card with a write protect switch you don't need to use nicOS-Utility-Suite and you don't need to boot in PUPMODE 5. You setup and customize the USB as necessary, shutdown and create a savefile as normal.
When that's done, just enable the write protect switch on the device and you're done. When booted normally the savefile is read, but NOTHING can be written back because of the write protect. I like this configuration because I can easily make changes/updates if needed and I can leave the USB always plugged into the computer.
wizard
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:35 pm
by wizard
@tammi806
Where do I learn about using this nicOS-Utility_Suite.
No expert on nic's Suite, but here's what I do in BW64:
*make all settings
*Menu>Utility>nicOS-Utility_Suite
**check Save2SFS
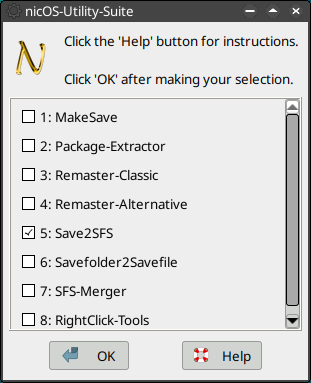
- nios1.png (32.07 KiB) Viewed 18809 times
**click OK
**check Choose Work Area, Save to ydrv, Exclude existing adrv and ydrv
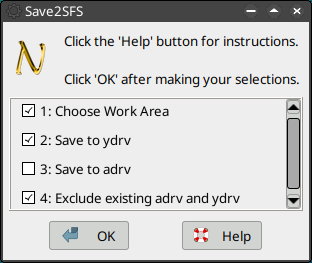
- nicos2.png (25.47 KiB) Viewed 18809 times
**click OK
**choose your work area
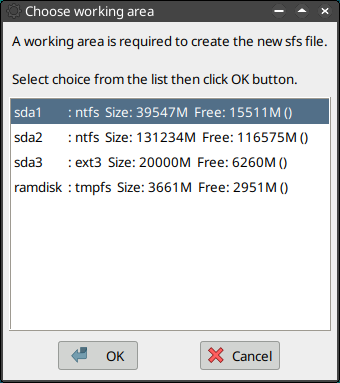
- nicos3.png (34.87 KiB) Viewed 18809 times
**click OK
Be prepared to wait. When it's complete, the work area directory will open
containing ydrv_dpup_10.0.1.sfs
*copy the ydrv file to the directory containing your Puppy boot files.
*rename or move your savefile so it will not be loaded.
Thanks
wizard
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:46 pm
by tammi806
I just discovered that nic os utility suite comes as default in Bookworm Pup64 so I'll use that one.
Okay so to use nic os utility and save my work do I need to install the distro as a frugal to a USB stick or can I just save my work to a USB stick and install as a live version each time.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:47 pm
by fredx181
dimkr wrote: ↑Tue Sep 05, 2023 7:22 pm
fredx181 wrote: ↑Tue Sep 05, 2023 7:19 pm
dmkir wrote:If spot can write files under /root, ....
How ? You mean if secret.txt contains the root password ?
No, every time X starts, xinit runs /root/.xinitrc, and every time root runs a shell, it runs /root/.bashrc, and every time the window manager is started, it runs the scripts in /root/Startup. If spot can write to any of these, an attacker that is able to execute arbitrary code inside an applications running as spot can write a script that will eventually run as root.
Ok, but trying to understand, if the scripts in /root/Startup are not proper (i.e. prevent ...?) then you got this problem, or ... ?
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:51 pm
by dimkr
If your browser running as spot is vulnerable and an attacker tricks it into writing rm -rf / to /root/.profile, this command will run as root (and succeed), not as spot.
What mechanism do you have to verify that no script under /root has been modified, and prevent such a thing?
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 7:51 pm
by tammi806
Okay I just remember that for some reason I cannot boot from my SD card when used in the usb card reader but I can save to it.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 8:03 pm
by tammi806
Okay so apparently I have to have the distro installed on a usb stick for nic utility to work so will have to do that in a bit.
The nic utility ran without a hitch and was straight forward.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 9:32 pm
by williwaw
tammi806 wrote: ↑Tue Sep 05, 2023 7:51 pm
Okay I just remember that for some reason I cannot boot from my SD card when used in the usb card reader but I can save to it.
often bios in some machines cannot deal with a card reader in the middle
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 10:06 pm
by proebler
williwaw wrote: ↑Tue Sep 05, 2023 9:32 pm
tammi806 wrote: ↑Tue Sep 05, 2023 7:51 pm
Okay I just remember that for some reason I cannot boot from my SD card when used in the usb card reader but I can save to it.
often bios in some machines cannot deal with a card reader in the middle
Beware also, that your SD card adapter/slot may not honor/recognize the SD card's lock position  .
.
Do test therefore, that you cannot write to the card once you have locked it!
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 10:45 pm
by tammi806
@wizard
Okay I apparently done the nic utility the right way as everything booted into Bookworm Pup64 and I no longer have a save icon and the event manager says PUPMODE=5.
Alright so when I want to do banking I just remove the USB stick I booted from is that correct.
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 11:24 pm
by wizard
@tammi806
Okay I just remember that for some reason I cannot boot from my SD card when used in the usb card reader but I can save to it.
Best then to just install to regular USB as per above, create a ydrv and boot in ram mode (You can use @dimkr suggestion to add pfix=ram to the grub kernel line to make this the default). This will let you boot from the USB and immediately remove it, thus preventing any chance of write back.
Thanks
wizard
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 11:29 pm
by wizard
@tammi806
Alright so when I want to do banking I just remove the USB stick I booted from is that correct.
Yes, the USB drive icons on the desktop should not show the USB is mounted and you can remove it as soon as you've booted.
Thanks
wizard
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 11:34 pm
by williwaw
wizard wrote: ↑Tue Sep 05, 2023 1:20 pm
@tammi806
So for banking and other sensitive personal use a better choice is to use a Linux distro that is not running as root user.
Not necessarily. With any Linux, the longer the system is on and connected to the internet, the greater the chance it can be compromised.
Doing these things can increase security for financial transactions:
*run a newer version of Puppy (Bookworm Pup64 in your case)
*install Puppy to a USB flash drive
*enable Puppy firewall
*run a newer version of a web browser
*configure your browser to "harden" it against attack (settings are a little different for each brand)
Once you are satisfied with your settings use nicOS-Utility_Suite to save your changes into a SFS file (this will now be read only and will load automatically).
Finally, boot from this USB with no savefile (also referred to as "ram only"), and conduct your transactions.
When finished, shut down, DO NOT SAVE, and remove your USB.
wizard
The dedicated USB seems worthwhile..
can you expand on how you "harden" your browser?
I used to think addons did what they claimed, but some do as they claim while others do just the opposite
Re: Is running as root a security risk?
Posted: Tue Sep 05, 2023 11:43 pm
by tammi806
Well I spoke to soon worked once and now nothing so I don't know. 
Re: Is running as root a security risk?
Posted: Wed Sep 06, 2023 12:30 am
by mikewalsh
dimkr wrote: ↑Tue Sep 05, 2023 7:51 pm
If your browser running as spot is vulnerable and an attacker tricks it into writing rm -rf / to /root/.profile, this command will run as root (and succeed), not as spot.
What mechanism do you have to verify that no script under /root has been modified, and prevent such a thing?
@dimkr :-
Hm. This sounds like the sort of thing you're involved with at work, yes?
Some weeks ago, I was reading an interview your guv'nor - Tal Kollender? - gave to Cybernews last year, where she was outlining her plans for what she wants Gytpol to achieve in the coming years. Although it sounds pretty specialized, it also sounds like it will fill a very definite "hole" in a lot of organisation's security strategies......IF they can perceive the value of what's being offered, that is.
https://cybernews.com/security/tal-koll ... gurations/
I confess to being impressed. Not only with the lady herself, but also the fact of her being a successful female 'player' in what is traditionally a male-dominated field of endeavour. Anything you read about infosec & cyber-security is almost always written by guys. More power to her, I say.
(I've always been interested in the etymology of words, and especially 'proper' names in language. I was reading an article on gHacks, which led to a link on WIRED.com.....and there I saw a link to this article. The name - Gytpol - was unusual, and it piqued my curiosity, so that's how I ended up reading it.)
---------------------------------------------
The bit about Gytpol's origins amused the hell out of me:-
"Gytpol was conceived in a café in Tel-Aviv on the back of a napkin. Sadly, the napkin no longer exists. But the concept I sketched that day is still very much the basis of what Gytpol is today."
Y'know, that's almost exactly how so many successful businesses - household names here in the UK, for the most part - started out. William "Bill" Lyons, chief designer at Jaguar back in the 1950s, sketched the original design for the E-type (the most successful classic sportscar EVER) on the back of an empty fag-packet. And almost forgot himself, and nearly chucked it in the rubbish-bin before remembering at the last moment what he'd scribbled there.... It's true!
----------------------------------
(I remembered taking a look at your Linked-In profile a while back. I tracked it down again, 'cos I was sure I recognised the name Gytpol. I followed the link to that piece you wrote on Medium (amongst others) - "Ramblings About The Open-Source Hobby". Love the stuff about the trumpet-playing, AND the way you like to fill a boring train-journey.....instead of staring vacantly into space, the way so many do. Which makes sense, thinking about it; if it works for you, why not?) 
I had NO idea you were as young as you are. I'd always pictured you in my mind as being the same sort of age-group as most of the rest of us. Which makes your own achievements all the more impressive, too.
You're a talented guy for one so young, Dima. In many ways, I'd say we're lucky to have you in the community. 
Mike. 
Re: Is running as root a security risk?
Posted: Wed Sep 06, 2023 1:18 am
by vtpup
I have never set up online banking with my bank. I don't keep a lot of money in the bank or elsewhere. I buy tools and land and other things that appreciate, AND can be used in living a simple lifestyle. I back up data once every few months on different drives each time. I also have a few computers with pretty much everything similar on them. One gets used every day. Some get used once every few months, some sit in a closet. I regularly update my browser, not by automatic update, but by new install, manually.
I run NoScript in my browser with ALL scripts blocked, and then run only the ones I need for a particular page temporarily. I've come to recognize the essential ones. If a page tries to run too many scripts, I just skip it as not worth my time. The browser is set to accept cookies for the session only, then delete. I don't keep history beyond the session. I use a hosts file from one of the known protective sources. I don't store passwords on my computer. I use an algorithm in my head to generate and remember passwords. I have a limited number of people I email and receive mail from. I don't open dumb emails, emails warning of threats, emails from myself, emails from names I don't recognize. If there is any question about a particular email, I "view" it "as source". and examine the content and header, before deleting or opening it.
I replace internal disk drives probably once every year or so, and keep the old one as backup. I download new Puppy versions to install on a new disk rather than imaging the old one over.
Is this any guarantee? Nope. Have I felt reasonably secure with Puppy. Yup. Have I felt less secure with other OS's Yup. Have I lost data in or functionality in some of them, Yup. Do I feel that I can recover a reasonable amount of data in the case of loss now on Puppy? Yup. Have I ever lost data on Puppy? Yup, but due to my human error, not malware. And I was able to recover it.
We each have strategies for survival. This is just mine.
Re: Is running as root a security risk?
Posted: Wed Sep 06, 2023 1:36 am
by ozsouth
@tammi806 - glad you're nearing a solution. Don't give up or let your age concern you - many of us here are 60 - 80 year old tinkerers.
@Grey - -re 'gangs' - I should have put that in quotes - the 1st 2 lines were the media headline (& alphv made ransom demands).
Re: Is running as root a security risk?
Posted: Wed Sep 06, 2023 3:00 am
by tammi806
ozsouth wrote: ↑Wed Sep 06, 2023 1:36 am
@tammi806 - glad you're nearing a solution. Don't give up or let your age concern you - many of us here are 60 - 80 year old tinkerers.
Thanks @ozsouth I did get it to work once but for some reason it didn't hold but yes I'll give it another go tomorrow just get frustrated.
I'll hang in there.
Thanks. 