Ok seems to be selecting sfs and removing the constructed mounts after running.
There remains a technical issue re. read only mounts / aufs that I admit to not understanding.
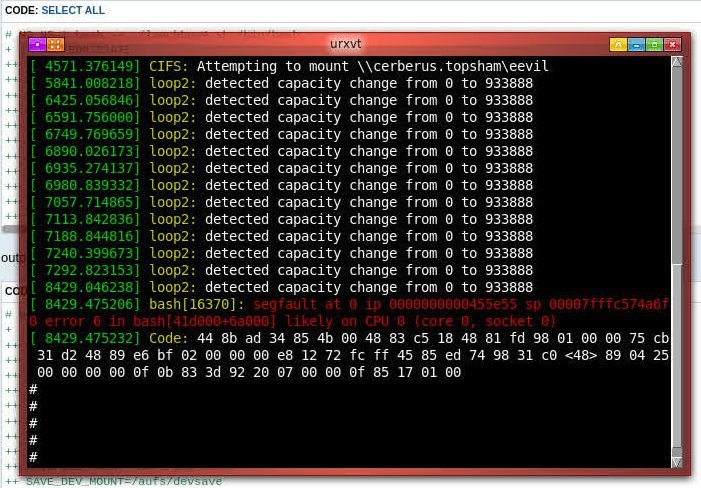
The segfault must relate to missing bits of the chroot environment that I have not supplied.
Code does seem to half work under a ram session, but under a savefile we get the output below.
" check your boot parameters (you may need to boot with 'pfix=nocopy' in order to use sandbox) " have tried this [TAB on the fd loader allows boot parms but no difference with "nocopy"].
The script below is not intended for use.
Code: Select all
#!/bin/sh
# James Budiono 2011, 2013, 2015, 2017, 2018, 2020
# Puppy test/compilation sandbox
# Uses tmpfs instead of an rw image, allows choosing which SFS to use
# Run this from the terminal.
# Version 12 - (2020) env NO_NS=1 don't use namespace, chroot only
# 0. Directory locations
. $BOOTSTATE_PATH # AUFS_ROOT_ID
[ "$NOT_USING_AUFS" ] && exit 1
XTERM="defaultterm"
SANDBOX_ROOT="/mnt/sb"
FAKEROOT="$SANDBOX_ROOT/fakeroot" # Mounted chroot location of sandbox - fake root
SANDBOX_TMPFS="$SANDBOX_ROOT/sandbox" # Mounted rw location of tmpfs used for sandbox
SANDBOX_ID=""
TMPFILE=$(mktemp -p /tmp)
# Debug prints to verify paths
echo "FAKEROOT: $FAKEROOT"
echo "SANDBOX_TMPFS: $SANDBOX_TMPFS"
# Clean up mounts if we are accidentally killed
trap 'umountall' 1
umountall() {
{
echo "Unmounting $FAKEROOT$SANDBOX_TMPFS"
echo "Unmounting $FAKEROOT"
umount -l "$FAKEROOT$SANDBOX_TMPFS"
umount -l "$FAKEROOT/tmp"
umount -l "$FAKEROOT/proc"
umount -l "$FAKEROOT/sys"
umount -l "$FAKEROOT/dev/pts" "$FAKEROOT/dev/shm" "$FAKEROOT/dev"
umount -l "$FAKEROOT"
umount -l "$SANDBOX_TMPFS"
rmdir "$FAKEROOT"
rmdir "$SANDBOX_TMPFS"
echo "UNMOUNTED! by unmountall"
sleep 5
} 2> /dev/null
}
die() {
echo "$1"
exit 1
}
# 0.1 Must be root
[ $(id -u) -ne 0 ] && die "You must be root to use sandbox."
# 0.2 Cannot launch sandbox within sandbox
grep -q "$SANDBOX_ROOT" /sys/fs/aufs/$AUFS_ROOT_ID/br0 && die "Cannot launch sandbox within sandbox."
# 0.3 Help
case "$1" in
--help|-h)
echo "Usage: ${0##*/} [cmd [args]]"
echo "Starts an in-memory (throwaway) sandbox. Type 'exit' to leave."
exit
esac
# 0.4 If not running from terminal but in Xorg, launch via terminal
! [ -t 0 ] && [ -n "$DISPLAY" ] && exec "$XTERM" -e "$0" "$@"
! [ -t 0 ] && exit
# 0.5 Is this the first sandbox? If not, create another name for mountpoints
if grep -q "$FAKEROOT" /proc/mounts; then
FAKEROOT=$(mktemp -d -p "$SANDBOX_ROOT" "${FAKEROOT##*/}.XXXXXXX")
SANDBOX_ID=".$(basename "$FAKEROOT")"
SANDBOX_TMPFS="$SANDBOX_ROOT/sandbox$SANDBOX_ID"
rmdir "$FAKEROOT"
fi
# 1. Get aufs system-id for the root filesystem
[ -z "$AUFS_ROOT_ID" ] && AUFS_ROOT_ID=$(awk '{ if ($2 == "/" && $3 == "aufs") { match($4,/si=[0-9a-f]*/); print "si_" substr($4,RSTART+3,RLENGTH-3) } }' /proc/mounts)
# 2. Detect SFS files and add them to items
items=$(ls /mnt/sda4/*.sfs 2>/dev/null | awk '{print $0, "[ ]"}')
# 3. Ask user to choose the SFS
[ -z "$items" ] && die "No SFS files found."
dialog --separate-output --backtitle "tmpfs sandbox" --title "sandbox config" \
--checklist "Choose which SFS you want to use" 0 60 10 $items 2> "$TMPFILE"
chosen="$(cat "$TMPFILE")"
clear
[ -z "$chosen" ] && die "Cancelled or no SFS is chosen, exiting."
# 4. Convert chosen SFS to robranches
robranches=""
for a in $chosen; do
robranches="$robranches $a"
done
rm "$TMPFILE"
# 5. Make the mountpoints if not exist yet
mkdir -p "$FAKEROOT" "$SANDBOX_TMPFS" "$FAKEROOT/etc" "$FAKEROOT/dev" "$FAKEROOT/sys" "$FAKEROOT/proc" "$FAKEROOT/tmp"
# Check if the directories are writable
if [ ! -w "$FAKEROOT/etc" ] || [ ! -w "$FAKEROOT/dev" ] || [ ! -w "$FAKEROOT/sys" ] || [ ! -w "$FAKEROOT/proc" ] || [ ! -w "$FAKEROOT/tmp" ]; then
die "Error: One or more necessary directories are not writable. Please check the file system permissions."
fi
# 6.0 Remount chroot filesystem as read-write
ls -ld "$FAKEROOT"
mount -o remount,rw "$FAKEROOT"
echo "Remounted $FAKEROOT as read-write"
# 6.1 Mount each selected SFS file
for sfs_file in $chosen; do
if mount -o loop "$sfs_file" "$FAKEROOT"; then
echo "Mounted $sfs_file to $FAKEROOT"
else
die "Failed to mount $sfs_file to $FAKEROOT"
fi
done
# 8. Sandbox is ready, now just need to mount other supports - pts, proc, sysfs, usb, and tmp
mkdir -p "$FAKEROOT$SANDBOX_TMPFS" # Fix path concatenation here
mount -o bind "$SANDBOX_TMPFS" "$FAKEROOT$SANDBOX_TMPFS" # So we can access it within the sandbox
mount -o rbind /dev "$FAKEROOT/dev"
mount -t sysfs none "$FAKEROOT/sys"
mount -t proc none "$FAKEROOT/proc"
mount -o bind /tmp "$FAKEROOT/tmp"
# 9. Optional copy, to enable running sandbox-ed xwin
cp /usr/share/sandbox/* "$FAKEROOT/usr/bin" 2> /dev/null
# 10. Identify ourselves as in sandbox - and we're good to go!
echo -e '\nexport PS1="sandbox'"${SANDBOX_ID}"'# "'
echo -e '\nexport PS1="sandbox'"${SANDBOX_ID}"'# "' >> "$FAKEROOT/etc/shinit"
sed -i -e '/^PS1/ s/^.*$/PS1="sandbox'"${SANDBOX_ID}"'# "/' "$FAKEROOT/etc/profile.local" 2> /dev/null
# 11. Run sandbox in namespace if possible (pid+mount), otherwise run chroot only
echo "[the vasty deep awaits ye] ... "
if [ "$NO_NS" ] || ! command -v unshare > /dev/null 2>&1; then
echo "Warning: sandbox runing in chroot-mode; if this does not work, check your"
echo "boot parameters (you may need to boot with 'pfix=nocopy' in order to use sandbox)"
echo
echo "sandbox will start now - exit from the shell to leave the sandbox."
echo "chroot $FAKEROOT ${@:-sh} [in 5 seconds...]"
echo
sleep 5
chroot "$FAKEROOT" "${@:-sh}"
sleep 5
umount -l "$FAKEROOT"
rm -R "$FAKEROOT"
else
echo "Notice: sandbox will try to run in a namespace ... "
echo " ... if this does not work it's your business not ours!"
echo
if command -v dumb-init > /dev/null; then
dumb-init unshare -pf --mount-proc chroot "$FAKEROOT" "${@:-sh}"
else
unshare -pf --mount-proc chroot "$FAKEROOT" "${@:-sh}"
fi
fi
echo
echo "UNMOUNT! in 10 seconds..."
sleep 10
umountall
echo "Done."
sleep 10
... output ...
Code: Select all
# NO_NS=1 bash -x ./lunchbox4.sh /bin/bash
+ . /etc/BOOTSTATE
++ GENUINE_FATDOG_INITRD=true
++ AUFS_ROOT=/aufs
++ BASELINE_MOUNT=/aufs/pup_init
++ MODULE_SFS_MOUNT=/aufs/kernel-modules
++ SAVE_DEV_PROTO=/aufs/devsave
++ SAVEFILE_PROTO=/fd64save.ext4
++ MULTI_PREFIX=multi-
++ BASE_SFS_MOUNT=/aufs/pup_ro
++ SAVEFILE_MOUNT=/aufs/pup_save
++ SAVE_DEV_MOUNT=/aufs/devsave
++ BASE_SFS_PATH=/fd64.sfs
++ SAVEFILE_PATH=fd64save-20240521
++ SAVEFILE_DEVICE=/dev/sda4
++ SAVEFILE_BIND=true
++ AUFS_ROOT_ID=si_d838a1a5bf16dcd7
+ '[' '' ']'
+ XTERM=defaultterm
+ SANDBOX_ROOT=/mnt/sb
+ FAKEROOT=/mnt/sb/fakeroot
+ SANDBOX_TMPFS=/mnt/sb/sandbox
+ SANDBOX_ID=
++ mktemp -p /tmp
+ TMPFILE=/tmp/tmp.DXqjz3TxIs
+ echo 'FAKEROOT: /mnt/sb/fakeroot'
FAKEROOT: /mnt/sb/fakeroot
+ echo 'SANDBOX_TMPFS: /mnt/sb/sandbox'
SANDBOX_TMPFS: /mnt/sb/sandbox
+ trap umountall 1
++ id -u
+ '[' 0 -ne 0 ']'
+ grep -q /mnt/sb /sys/fs/aufs/si_d838a1a5bf16dcd7/br0
+ case "$1" in
+ '[' -t 0 ']'
+ '[' -t 0 ']'
+ grep -q /mnt/sb/fakeroot /proc/mounts
+ '[' -z si_d838a1a5bf16dcd7 ']'
++ ls /mnt/sda4/32bit-fd64_813.sfs /mnt/sda4/32bit-fd64_901.sfs /mnt/sda4/compiz-reloaded-0.8.16-x86_64-2.sfs /mnt/sda4/compiz-reloaded-2024.02-x86_64-1.sfs /mnt/sda4/fd64-devx_813.sfs /mnt/sda4/fd64-devx_901.sfs /mnt/sda4/fd64.sfs /mnt/sda4/google-earth-2019.02.sfs /mnt/sda4/kernel-source-5.19.14.sfs /mnt/sda4/kernel-source-6.1.46.sfs /mnt/sda4/signal-6.20.0.sfs /mnt/sda4/wine-7.11-i686-1.sfs /mnt/sda4/wine-8.6-i686-1.sfs /mnt/sda4/xfce-4.18-x86_64.sfs /mnt/sda4/zoom-5.15.3-x86_64.sfs
++ awk '{print $0, "[ ]"}'
+ items='/mnt/sda4/32bit-fd64_813.sfs [ ]
/mnt/sda4/32bit-fd64_901.sfs [ ]
/mnt/sda4/compiz-reloaded-0.8.16-x86_64-2.sfs [ ]
/mnt/sda4/compiz-reloaded-2024.02-x86_64-1.sfs [ ]
/mnt/sda4/fd64-devx_813.sfs [ ]
/mnt/sda4/fd64-devx_901.sfs [ ]
/mnt/sda4/fd64.sfs [ ]
/mnt/sda4/google-earth-2019.02.sfs [ ]
/mnt/sda4/kernel-source-5.19.14.sfs [ ]
/mnt/sda4/kernel-source-6.1.46.sfs [ ]
/mnt/sda4/signal-6.20.0.sfs [ ]
/mnt/sda4/wine-7.11-i686-1.sfs [ ]
/mnt/sda4/wine-8.6-i686-1.sfs [ ]
/mnt/sda4/xfce-4.18-x86_64.sfs [ ]
/mnt/sda4/zoom-5.15.3-x86_64.sfs [ ]'
+ '[' -z '/mnt/sda4/32bit-fd64_813.sfs [ ]
/mnt/sda4/32bit-fd64_901.sfs [ ]
/mnt/sda4/compiz-reloaded-0.8.16-x86_64-2.sfs [ ]
/mnt/sda4/compiz-reloaded-2024.02-x86_64-1.sfs [ ]
/mnt/sda4/fd64-devx_813.sfs [ ]
/mnt/sda4/fd64-devx_901.sfs [ ]
/mnt/sda4/fd64.sfs [ ]
/mnt/sda4/google-earth-2019.02.sfs [ ]
/mnt/sda4/kernel-source-5.19.14.sfs [ ]
/mnt/sda4/kernel-source-6.1.46.sfs [ ]
/mnt/sda4/signal-6.20.0.sfs [ ]
/mnt/sda4/wine-7.11-i686-1.sfs [ ]
/mnt/sda4/wine-8.6-i686-1.sfs [ ]
/mnt/sda4/xfce-4.18-x86_64.sfs [ ]
/mnt/sda4/zoom-5.15.3-x86_64.sfs [ ]' ']'
+ dialog --separate-output --backtitle 'tmpfs sandbox' --title 'sandbox config' --checklist 'Choose which SFS you want to use' 0 60 10 /mnt/sda4/32bit-fd64_813.sfs '[' ']' /mnt/sda4/32bit-fd64_901.sfs '[' ']' /mnt/sda4/compiz-reloaded-0.8.16-x86_64-2.sfs '[' ']' /mnt/sda4/compiz-reloaded-2024.02-x86_64-1.sfs '[' ']' /mnt/sda4/fd64-devx_813.sfs '[' ']' /mnt/sda4/fd64-devx_901.sfs '[' ']' /mnt/sda4/fd64.sfs '[' ']' /mnt/sda4/google-earth-2019.02.sfs '[' ']' /mnt/sda4/kernel-source-5.19.14.sfs '[' ']' /mnt/sda4/kernel-source-6.1.46.sfs '[' ']' /mnt/sda4/signal-6.20.0.sfs '[' ']' /mnt/sda4/wine-7.11-i686-1.sfs '[' ']' /mnt/sda4/wine-8.6-i686-1.sfs '[' ']' /mnt/sda4/xfce-4.18-x86_64.sfs '[' ']' /mnt/sda4/zoom-5.15.3-x86_64.sfs '[' ']'
tmpfs sandbox
──────────────────────────────────────────────────────────────────────────────
┌─────────────────────sandbox config───────────────────────┐
│ Choose which SFS you want to use │
│ ┌──────────────────────────────────────────────────────┐ │
│ │[ ] /mnt/sda4/32bit-fd64_813.sfs [ │ │
│ │[ ] /mnt/sda4/32bit-fd64_901.sfs [ │ │
│ │[ ] /mnt/sda4/compiz-reloaded-0.8.16-x86_64-2.sfs [ │ │
│ │[ ] /mnt/sda4/compiz-reloaded-2024.02-x86_64-1.sfs [ │ │
│ │[ ] /mnt/sda4/fd64-devx_813.sfs [ │ │
│ │[ ] /mnt/sda4/fd64-devx_901.sfs [ │ │
│ │[*] /mnt/sda4/fd64.sfs [ │ │
│ │[ ] /mnt/sda4/google-earth-2019.02.sfs [ │ │
│ │[ ] /mnt/sda4/kernel-source-5.19.14.sfs [ │ │
│ │[ ] /mnt/sda4/kernel-source-6.1.46.sfs [ │ │
│ │[ ] /mnt/sda4/signal-6.20.0.sfs [ │ │
│ └────↓(+)──────────────────────────────────────73%─────┘ │
├──────────────────────────────────────────────────────────┤
│ < OK > <Cancel> │
└──────────────────────────────────────────────────────────┘
++ cat /tmp/tmp.DXqjz3TxIs
+ chosen=/mnt/sda4/fd64.sfs
+ clear
+ '[' -z /mnt/sda4/fd64.sfs ']'
+ robranches=
+ for a in $chosen
+ robranches=' /mnt/sda4/fd64.sfs'
+ rm /tmp/tmp.DXqjz3TxIs
+ mkdir -p /mnt/sb/fakeroot /mnt/sb/sandbox /mnt/sb/fakeroot/etc /mnt/sb/fakeroot/dev /mnt/sb/fakeroot/sys /mnt/sb/fakeroot/proc /mnt/sb/fakeroot/tmp
+ '[' '!' -w /mnt/sb/fakeroot/etc ']'
+ '[' '!' -w /mnt/sb/fakeroot/dev ']'
+ '[' '!' -w /mnt/sb/fakeroot/sys ']'
+ '[' '!' -w /mnt/sb/fakeroot/proc ']'
+ '[' '!' -w /mnt/sb/fakeroot/tmp ']'
+ ls -ld /mnt/sb/fakeroot
drwxr-xr-x 7 root root 4096 May 22 21:26 /mnt/sb/fakeroot
+ mount -o remount,rw /mnt/sb/fakeroot
mount: /mnt/sb/fakeroot: mount point not mounted or bad option.
dmesg(1) may have more information after failed mount system call.
+ echo 'Remounted /mnt/sb/fakeroot as read-write'
Remounted /mnt/sb/fakeroot as read-write
+ for sfs_file in $chosen
+ mount -o loop /mnt/sda4/fd64.sfs /mnt/sb/fakeroot
+ echo 'Mounted /mnt/sda4/fd64.sfs to /mnt/sb/fakeroot'
Mounted /mnt/sda4/fd64.sfs to /mnt/sb/fakeroot
+ mkdir -p /mnt/sb/fakeroot/mnt/sb/sandbox
mkdir: cannot create directory ‘/mnt/sb/fakeroot/mnt/sb’: Read-only file system
+ mount -o bind /mnt/sb/sandbox /mnt/sb/fakeroot/mnt/sb/sandbox
mount: /mnt/sb/fakeroot/mnt/sb/sandbox: mount point does not exist.
dmesg(1) may have more information after failed mount system call.
+ mount -o rbind /dev /mnt/sb/fakeroot/dev
+ mount -t sysfs none /mnt/sb/fakeroot/sys
+ mount -t proc none /mnt/sb/fakeroot/proc
+ mount -o bind /tmp /mnt/sb/fakeroot/tmp
+ cp /usr/share/sandbox/lxc /usr/share/sandbox/wmexit /usr/share/sandbox/xwin /mnt/sb/fakeroot/usr/bin
+ echo -e '\nexport PS1="sandbox# "'
export PS1="sandbox# "
+ echo -e '\nexport PS1="sandbox# "'
./lunchbox4.sh: line 131: /mnt/sb/fakeroot/etc/shinit: Read-only file system
+ sed -i -e '/^PS1/ s/^.*$/PS1="sandbox# "/' /mnt/sb/fakeroot/etc/profile.local
+ echo '[the vasty deep awaits ye] ... '
[the vasty deep awaits ye] ...
+ '[' 1 ']'
+ echo 'Warning: sandbox runing in chroot-mode; if this does not work, check your'
Warning: sandbox runing in chroot-mode; if this does not work, check your
+ echo 'boot parameters (you may need to boot with '\''pfix=nocopy'\'' in order to use sandbox)'
boot parameters (you may need to boot with 'pfix=nocopy' in order to use sandbox)
+ echo
+ echo 'sandbox will start now - exit from the shell to leave the sandbox.'
sandbox will start now - exit from the shell to leave the sandbox.
+ echo 'chroot /mnt/sb/fakeroot /bin/bash [in 5 seconds...]'
chroot /mnt/sb/fakeroot /bin/bash [in 5 seconds...]
+ echo
+ sleep 5
+ chroot /mnt/sb/fakeroot /bin/bash
./lunchbox4.sh: line 161: 14077 Segmentation fault chroot "$FAKEROOT" "${@:-sh}"
+ sleep 5
+ umount -l /mnt/sb/fakeroot
+ rm -R /mnt/sb/fakeroot
+ echo
+ echo 'UNMOUNT! in 10 seconds...'
UNMOUNT! in 10 seconds...
+ sleep 10
+ umountall
Unmounting /mnt/sb/fakeroot/mnt/sb/sandbox
Unmounting /mnt/sb/fakeroot
UNMOUNTED! by unmountall
+ echo Done.
Done.
+ sleep 10
#
output in namespace mode...
Code: Select all
# bash -x ./lunchbox4.sh /bin/bash
+ . /etc/BOOTSTATE
++ GENUINE_FATDOG_INITRD=true
++ AUFS_ROOT=/aufs
++ BASELINE_MOUNT=/aufs/pup_init
++ MODULE_SFS_MOUNT=/aufs/kernel-modules
++ SAVE_DEV_PROTO=/aufs/devsave
++ SAVEFILE_PROTO=/fd64save.ext4
++ MULTI_PREFIX=multi-
++ BASE_SFS_MOUNT=/aufs/pup_ro
++ SAVEFILE_MOUNT=/aufs/pup_save
++ SAVE_DEV_MOUNT=/aufs/devsave
++ BASE_SFS_PATH=/fd64.sfs
++ SAVEFILE_PATH=fd64save-20240521
++ SAVEFILE_DEVICE=/dev/sda4
++ SAVEFILE_BIND=true
++ AUFS_ROOT_ID=si_d838a1a5bf16dcd7
+ '[' '' ']'
+ XTERM=defaultterm
+ SANDBOX_ROOT=/mnt/sb
+ FAKEROOT=/mnt/sb/fakeroot
+ SANDBOX_TMPFS=/mnt/sb/sandbox
+ SANDBOX_ID=
++ mktemp -p /tmp
+ TMPFILE=/tmp/tmp.NdktXXJl9V
+ echo 'FAKEROOT: /mnt/sb/fakeroot'
FAKEROOT: /mnt/sb/fakeroot
+ echo 'SANDBOX_TMPFS: /mnt/sb/sandbox'
SANDBOX_TMPFS: /mnt/sb/sandbox
+ trap umountall 1
++ id -u
+ '[' 0 -ne 0 ']'
+ grep -q /mnt/sb /sys/fs/aufs/si_d838a1a5bf16dcd7/br0
+ case "$1" in
+ '[' -t 0 ']'
+ '[' -t 0 ']'
+ grep -q /mnt/sb/fakeroot /proc/mounts
+ '[' -z si_d838a1a5bf16dcd7 ']'
++ awk '{print $0, "[ ]"}'
++ ls /mnt/sda4/32bit-fd64_813.sfs /mnt/sda4/32bit-fd64_901.sfs /mnt/sda4/compiz-reloaded-0.8.16-x86_64-2.sfs /mnt/sda4/compiz-reloaded-2024.02-x86_64-1.sfs /mnt/sda4/fd64-devx_813.sfs /mnt/sda4/fd64-devx_901.sfs /mnt/sda4/fd64.sfs /mnt/sda4/google-earth-2019.02.sfs /mnt/sda4/kernel-source-5.19.14.sfs /mnt/sda4/kernel-source-6.1.46.sfs /mnt/sda4/signal-6.20.0.sfs /mnt/sda4/wine-7.11-i686-1.sfs /mnt/sda4/wine-8.6-i686-1.sfs /mnt/sda4/xfce-4.18-x86_64.sfs /mnt/sda4/zoom-5.15.3-x86_64.sfs
+ items='/mnt/sda4/32bit-fd64_813.sfs [ ]
/mnt/sda4/32bit-fd64_901.sfs [ ]
/mnt/sda4/compiz-reloaded-0.8.16-x86_64-2.sfs [ ]
/mnt/sda4/compiz-reloaded-2024.02-x86_64-1.sfs [ ]
/mnt/sda4/fd64-devx_813.sfs [ ]
/mnt/sda4/fd64-devx_901.sfs [ ]
/mnt/sda4/fd64.sfs [ ]
/mnt/sda4/google-earth-2019.02.sfs [ ]
/mnt/sda4/kernel-source-5.19.14.sfs [ ]
/mnt/sda4/kernel-source-6.1.46.sfs [ ]
/mnt/sda4/signal-6.20.0.sfs [ ]
/mnt/sda4/wine-7.11-i686-1.sfs [ ]
/mnt/sda4/wine-8.6-i686-1.sfs [ ]
/mnt/sda4/xfce-4.18-x86_64.sfs [ ]
/mnt/sda4/zoom-5.15.3-x86_64.sfs [ ]'
+ '[' -z '/mnt/sda4/32bit-fd64_813.sfs [ ]
/mnt/sda4/32bit-fd64_901.sfs [ ]
tmpfs sandbox
──────────────────────────────────────────────────────────────────────────────
┌─────────────────────sandbox config───────────────────────┐
+ '[' -z /mnt/sda4/fd64.sfs ']'
+ robranches=
+ for a in $chosen
+ robranches=' /mnt/sda4/fd64.sfs'
+ rm /tmp/tmp.NdktXXJl9V
+ mkdir -p /mnt/sb/fakeroot /mnt/sb/sandbox /mnt/sb/fakeroot/etc /mnt/sb/fakeroot/dev /mnt/sb/fakeroot/sys /mnt/sb/fakeroot/proc /mnt/sb/fakeroot/tmp
+ '[' '!' -w /mnt/sb/fakeroot/etc ']'
+ '[' '!' -w /mnt/sb/fakeroot/dev ']'
+ '[' '!' -w /mnt/sb/fakeroot/sys ']'
+ '[' '!' -w /mnt/sb/fakeroot/proc ']'
+ '[' '!' -w /mnt/sb/fakeroot/tmp ']'
+ ls -ld /mnt/sb/fakeroot
drwxr-xr-x 7 root root 4096 May 22 21:45 /mnt/sb/fakeroot
+ mount -o remount,rw /mnt/sb/fakeroot
mount: /mnt/sb/fakeroot: mount point not mounted or bad option.
dmesg(1) may have more information after failed mount system call.
+ echo 'Remounted /mnt/sb/fakeroot as read-write'
Remounted /mnt/sb/fakeroot as read-write
+ for sfs_file in $chosen
+ mount -o loop /mnt/sda4/fd64.sfs /mnt/sb/fakeroot
+ echo 'Mounted /mnt/sda4/fd64.sfs to /mnt/sb/fakeroot'
Mounted /mnt/sda4/fd64.sfs to /mnt/sb/fakeroot
+ mkdir -p /mnt/sb/fakeroot/mnt/sb/sandbox
mkdir: cannot create directory ‘/mnt/sb/fakeroot/mnt/sb’: Read-only file system
+ mount -o bind /mnt/sb/sandbox /mnt/sb/fakeroot/mnt/sb/sandbox
mount: /mnt/sb/fakeroot/mnt/sb/sandbox: mount point does not exist.
dmesg(1) may have more information after failed mount system call.
+ mount -o rbind /dev /mnt/sb/fakeroot/dev
+ mount -t sysfs none /mnt/sb/fakeroot/sys
+ mount -t proc none /mnt/sb/fakeroot/proc
+ mount -o bind /tmp /mnt/sb/fakeroot/tmp
+ cp /usr/share/sandbox/lxc /usr/share/sandbox/wmexit /usr/share/sandbox/xwin /mnt/sb/fakeroot/usr/bin
+ echo -e '\nexport PS1="sandbox# "'
export PS1="sandbox# "
+ echo -e '\nexport PS1="sandbox# "'
./lunchbox4.sh: line 131: /mnt/sb/fakeroot/etc/shinit: Read-only file system
+ sed -i -e '/^PS1/ s/^.*$/PS1="sandbox# "/' /mnt/sb/fakeroot/etc/profile.local
+ echo '[the vasty deep awaits ye] ... '
[the vasty deep awaits ye] ...
+ '[' '' ']'
+ command -v unshare
+ echo 'Notice: sandbox will try to run in a namespace ... '
Notice: sandbox will try to run in a namespace ...
+ echo ' ... if this does not work it'\''s your business not ours!'
... if this does not work it's your business not ours!
+ echo
+ command -v dumb-init
+ dumb-init unshare -pf --mount-proc chroot /mnt/sb/fakeroot /bin/bash
bash: cannot set terminal process group (-1): Inappropriate ioctl for device
bash: no job control in this shell
+ echo
+ echo 'UNMOUNT! in 10 seconds...'
UNMOUNT! in 10 seconds...
+ sleep 10
+ umountall
Unmounting /mnt/sb/fakeroot/mnt/sb/sandbox
Unmounting /mnt/sb/fakeroot
UNMOUNTED! by unmountall
+ echo Done.
Done.
+ sleep 10
#
- Screenshot(2).jpg (112.14 KiB) Viewed 1149 times